Threat Hunting - Simplifying The Beacon Analysis Process - Active
In part one of this two-part series, I described what is involved with performing a beacon analysis and why it is so important […]

From BumbleBee to Cobalt Strike: Steps of a BumbleBee intrusion
Enterprise Scale Threat Hunting: Network Beacon Detection with Unsupervised ML and KQL, by Mehmet Ergene, May, 2021
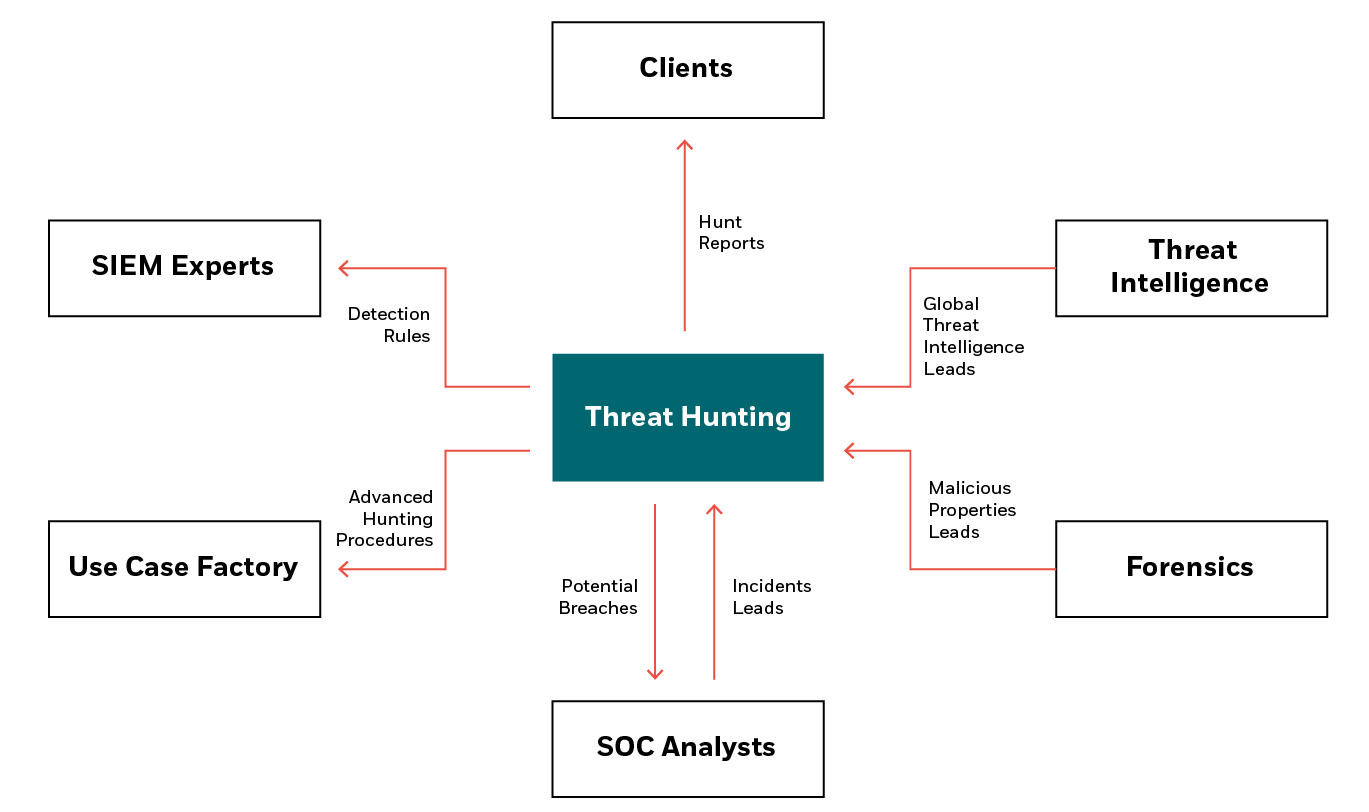
What is threat hunting? – CyberProof
Threat Hunting - Simplifying The Beacon Analysis Process - Active Countermeasures
Contact Tracing with Low Power Beacons for Active and Passive Data Management and Klika Tech Case Study

ICS Threat Hunting - They're Shootin' at the Lights! - Part 1
Patch Your WSO2: CVE-2022-29464 Exploited to Install Linux-Compatible Cobalt Strike Beacons, Other Malware

How effective is your cyber security threat hunting programme? - PwC UK
Modeling Securitized Products: Improving Valuation and Risk Analysis - Beacon Platform Inc.
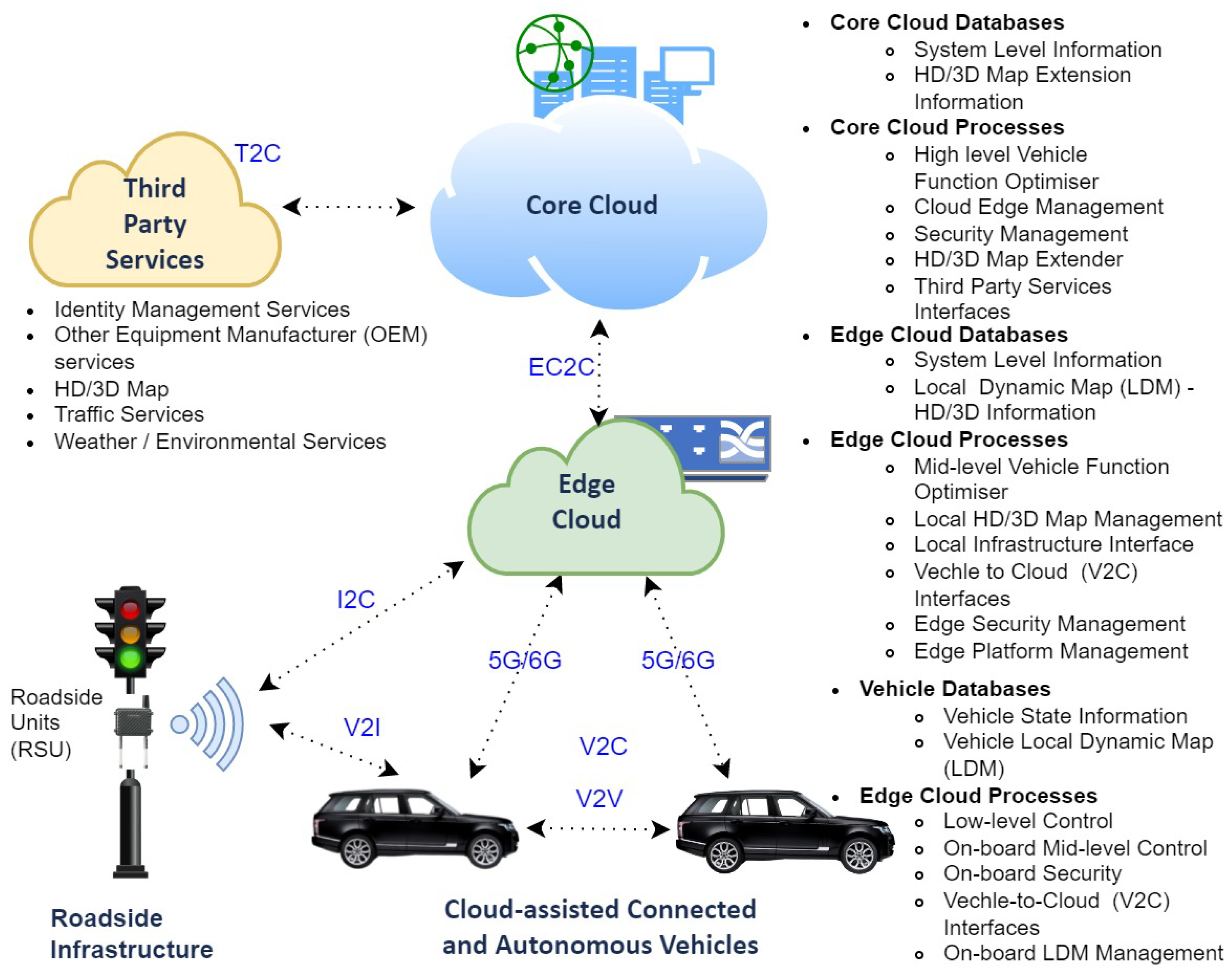
Sensors, Free Full-Text

My Saturday with Active Countermeasures

Hunt Training - Active Countermeasures

Threat Hunting - Simplifying The Beacon Analysis Process - Active Countermeasures
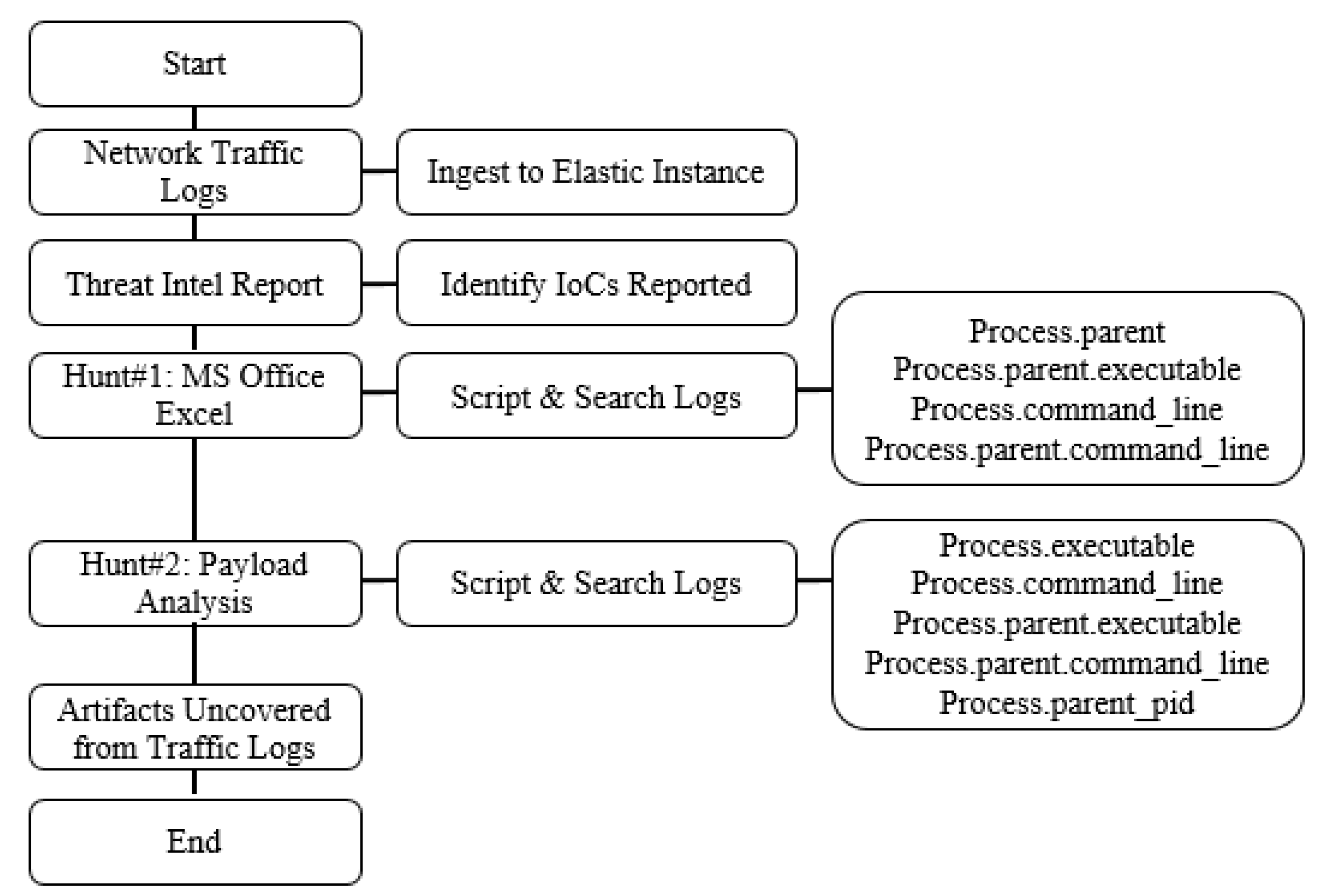
Electronics, Free Full-Text
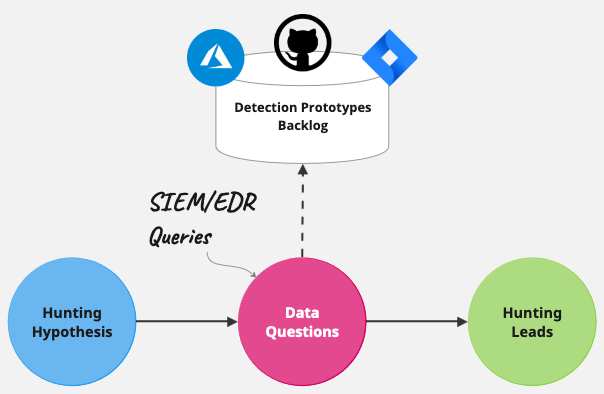
Beyond IOCs: Contextualized Leads from Analytics-Driven Threat Hunts, by Alex Teixeira




